About Client
CrowdSec is a hyper growth cybersecurity company with 300k+ installations. According to G2 it’s a market leader in 8+ categories.
Problem Statement
CrowdSec offers CTI data through their API. Lot of their enterprise customers want to consume this data using their own cybersecurity tools. Splunk SOAR (formerly Phantom) is one the most common tools used by enterprises. CrowdSec wanted to provide a Splunk SOAR app to their customers so they can consume CrowdSec CTI data in Splunk SOAR.
What is Splunk SOAR ?
It’s a Security Orchestration, Automation and Response (SOAR) platform. It’s used by many Fortune 500 companies. It allows users to automate their cybersecurity workflows consisting of multiple tools.
Solution
We decided to create a Splunk SOAR Connector App for CrowdSec. This App would add a new action to Splunk SOAR. This action would allow users to query CrowdSec CTI data for specified IP from Splunk SOAR itself.
Implementation
We used Splunk SOAR’s App Wizard to develop the app. The App Wizard generates a skeleton app which can be extended to add new features. The app is written in Python.
This is how the app provides data to the users:
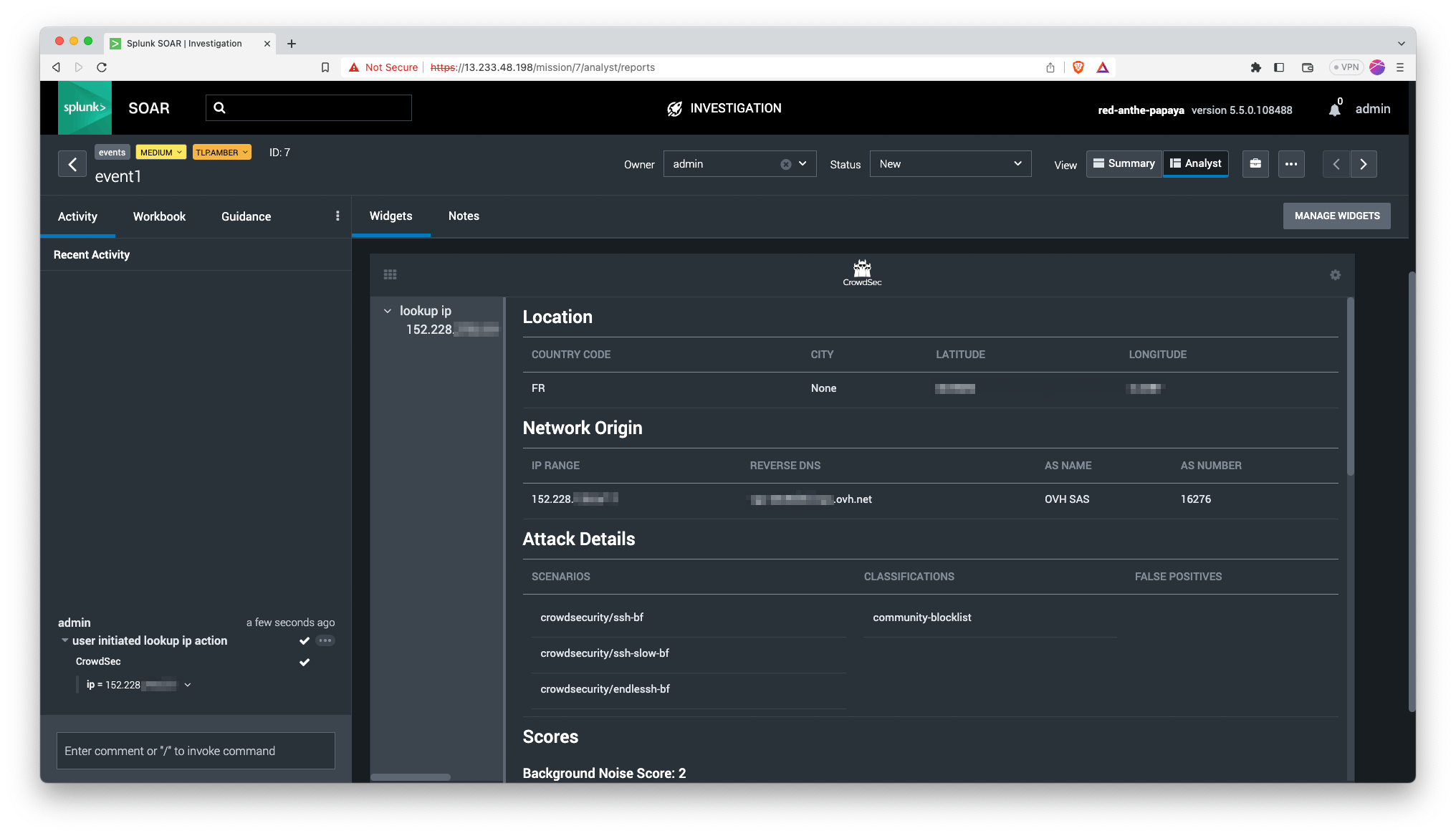
Challenges
Publishing the app on Splunkbase was a bit challenging. It’s straighforward to simply publish the app through the wizard, but on the Splunkbase the owner of app is Splunk. This is not ideal for CrowdSec. App publishers then have to contact Splunk to transfer the ownership of the app to them. We had to contact Splunk to transfer the ownership of the app to CrowdSec.
Results
The App is available on Splunkbase.
Source code is available on Splunk SOAR’s GitHub
Documentation is available at CrowdSec’s doc site