About Client
CrowdSec is a hyper growth cybersecurity company with 300k+ installations. According to G2 it’s a market leader in 8+ categories.
Problem Statement
CrowdSec offers CTI data through their API. Lot of their enterprise customers want to consume this data using their own cybersecurity tools. Splunk SIEM is one the most common tools used by enterprises. CrowdSec wanted to provide a Splunk app to their customers so they can consume CrowdSec CTI data in Splunk.
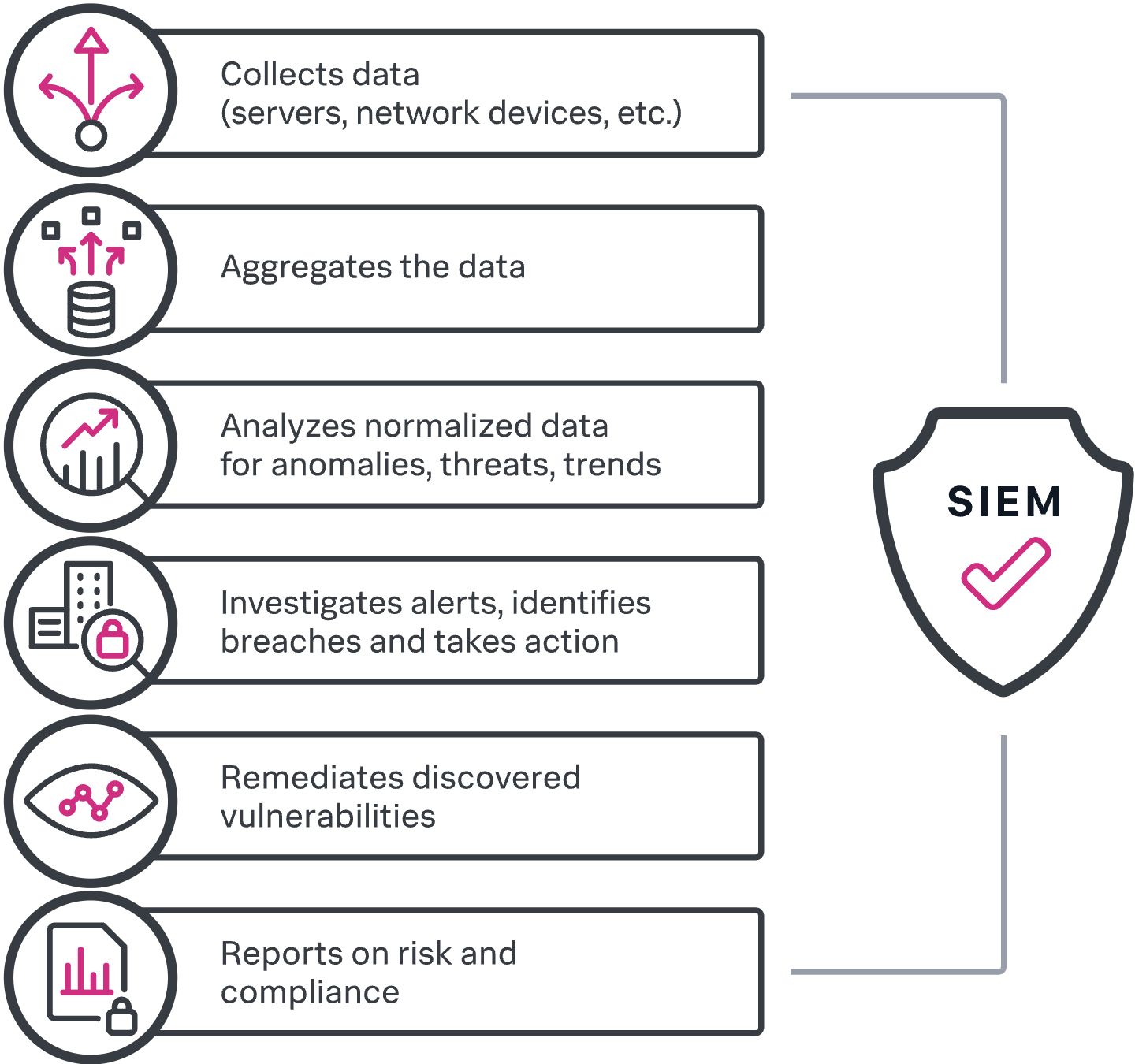
Splunk SIEM is a complex tool. It performs a lot of tasks like all SIEMs do. We had to find a way to integrate CrowdSec CTI data into Splunk SIEM which would be applicable to most of the existing workflows. This is supposed to be the first iteration of the app. CrowdSec wanted to add more features in the future according to the feedback from their customers.
Solution
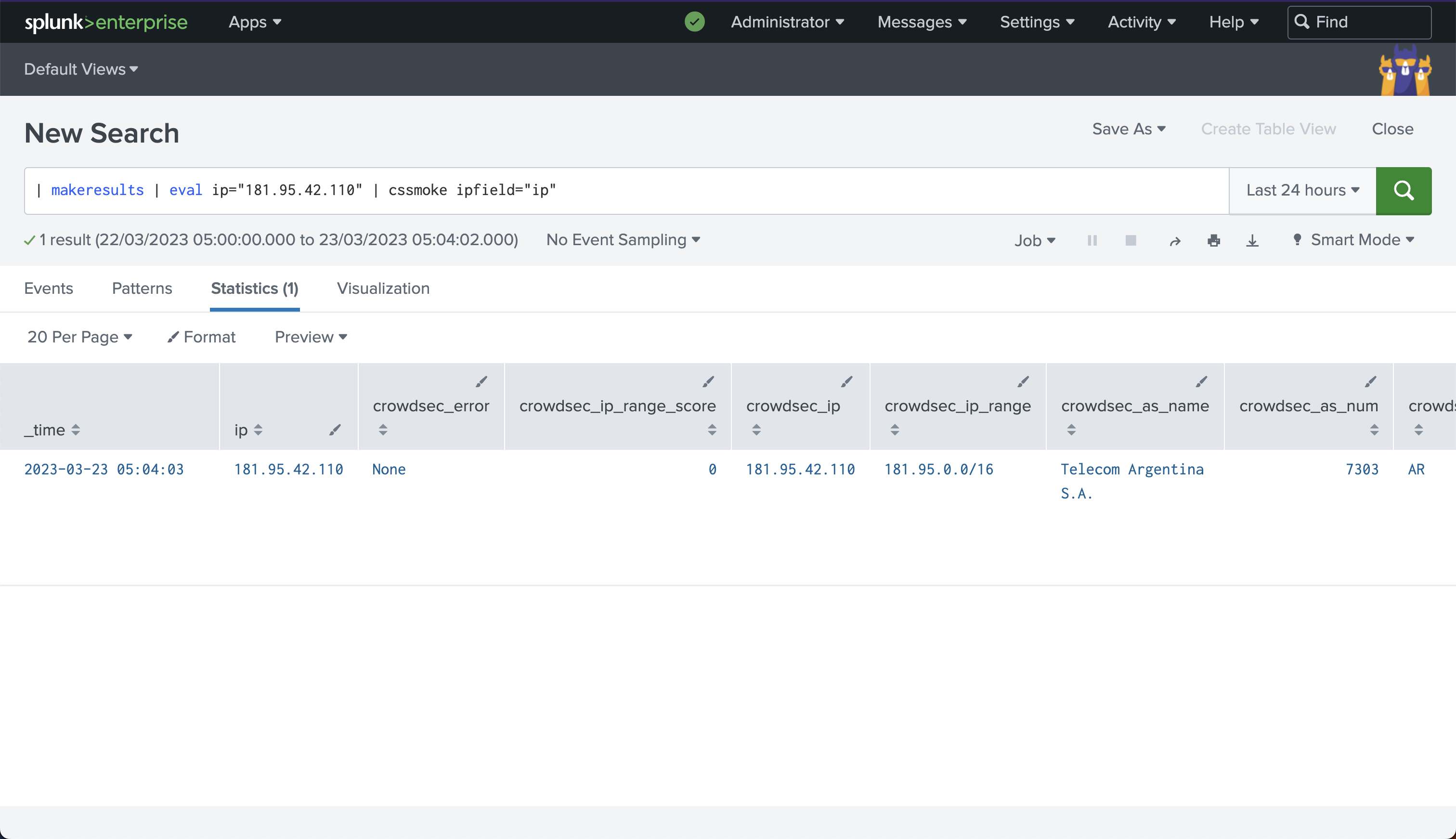
We decided to create a Splunk App for CrowdSec. This App would add a new command to Splunk SPL. This command would allow users to query CrowdSec CTI data from Splunk. The users would specify the index and the field where the IPs are stored. The command would then query the CrowdSec API and return the CTI data for the IPs.
Implementation
We used Python to implement the app. We used the official Splunk SDK for Python to implement the app.
We wrote a Github Action to automate the build process. The action would build the app and upload it to Splunkbase. It would also run various tests to ensure the app is compatible with Splunk.
This is how the app provides data to the users:
Challenges
The biggest challenge was to make the app as generic as possible. We researched lot of Splunk SIEM use cases and tried to make the app as generic as possible.
Results
The app is open source and available on GitHub. Lot of CrowdSec’s enterprise customers are using the app to consume CrowdSec CTI data in Splunk SIEM.
The app is also available on Splunkbase.
Documentation for the app is available here.